Amid Covid19 pandemic, and even prior, it seems as though cloud computing has become common grounds for companies of various fields, types and sizes, from small startups to enterprises – everyone is migrating to the cloud.
And this trend is happening for good reason. Benefits such as high availability, scalability and reliability, are some of the cloud’s strong points. Today it is so simple to launch a web application in the cloud, it takes a mere 10 minutes with AWS.
During the Corona pandemic, more and more businesses started e-commerce and online retail to keep their businesses alive, so they created web and mobile applications. The need for a speedy launch has, unfortunately, also caused a huge gap in the implementation of security best practices, making many such sites vulnerable to security hazards. So, how do you ensure security for that Web application which obviously will be exposed to the internet?
Cloud computing has Security as one of it’s core concepts and thus to keep your cloud environment secure, you as a business need to follow several rules such as limit access to least privilege, encrypt data at rest and in transit and also harden your Infruscure and keep those machines patched up. Web Applications are exposed to the internet and need to be accessed today from all over the world, using any platform. To add security to that application there is a use of a Web Application Firewall – WAF.
Cloud Providers have their solutions and best practices and there are several great 3rd party applications out there in the market to help companies with that. But, these kinds of products and services need constant maintenance, update signatures and block off attackers. Not all businesses can, nor do they know how to do that according to best practices. Configuring WAF rules can be challenging and burdensome to large and small organizations alike, especially for those who do not have dedicated security teams.
How can my business automate the Security of its web application?
AWS WAF is a security service that enables customers to create custom application-specific rules that can block common attacks on their web application.
AWS WAF Security Automations is an additional set of configurations made by CloudFormation template to help deploy a set of WAF rules to filter common web attacks.
At the core of the design is an AWS WAF web ACL that acts as a central inspection and decision point for all incoming requests. The WAF is made with pass-through nature, using services and basic rules to prevent simple attacks such as simple SQL-Injections. The additional layer of security with the automation is made with two main components:
- Analyzing logs for traces of suspicious behavior that can slow or harm the application, in addition to the inspection of the request content the rate per time interval is measured and gets blocked if a DDOS attack is suspected.
- Using API-Gateway as a honeypot and Lambda Functions the WAF automatically adds malicious IP’s to it’s web ACL and blocks them.
For example, if a bot is scanning your site for open api’s it will search for the “admin” access, something like admin.your-web-application.com, the security automations template detects this non-valid user action and triggers a lambda function that adds the IP of that bot to the block list.
But, what happens to valid users?
The automation is not interfering with valid-user actions, every request made to the application is inspected and compared to the normal behavior, only non-valid actions are blocked.
What kind of web-attacks are we talking about?
The system is built and made to block all kinds of common web attacks such as:
- HTTP Flood
- SQL Injection
- XSS
- Bad Bots
- DDOS
- Scanners and Probes
Even interaction with an IP recognized by one of the cybersecurity experts as malicious will be blocked.
The solution is made to protect Internet facing within the AWS infrastructure such as CloudFront and Application Load Balancers.
OK, How do I do that?
AWS published cloudformation templates that can be deployed via bash scripts. The documentation can be found here: https://github.com/awslabs/aws-waf-security-automations
The architecture: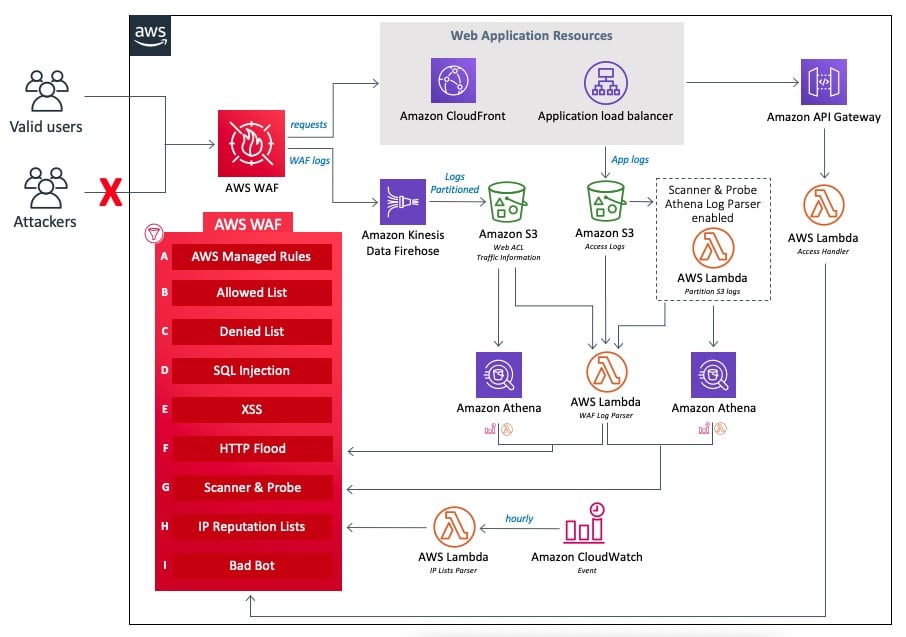
Not sure if this solution is the right one for you?
Book a free consultation call right here
Read our Cloudride & Radware’s Workload Protection services – eBook here

